iTracker
Mapping Compliance in Software and Data Supply Chains
iTracker
Mapping Compliance in Software and Data Supply Chains
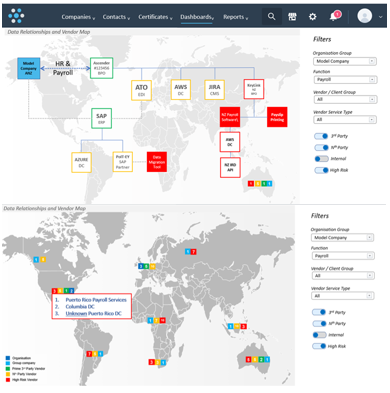
Visibility of the Nth-Party
iTracker is a compliance management software tool developed by P3 Audit that helps organizations manage their third-party suppliers and assess risks associated with those relationships.
The tool provides a centralized platform for tracking and monitoring compliance-related information, such as data privacy regulations, security protocols, and other industry-specific requirements.
It enables organizations to identify and mitigate risks associated with their third-party suppliers, ensure their data supply chain is secure and compliant with relevant regulations, and gain insights into their data supply chain through reporting and analytics features.
If you want to manage compliance and third-party risk quickly, safely and effectively, then click on the link below to schedule a demo.
The importance vendors play in your business continuity
On average over 180 vendors access a company’s network in a given week, and 85% of organisations are unaware of their data being accessed by Nth party processors who they have no direct relationship with. Vendor landscapes include illegitimate Nth party data handlers and left unmonitored will increase exposure to disruption of business critical processes.
Cyber-attacks originating via third parties are on the rise. 57% of organisations don’t know if their vendor safeguards are sufficient to prevent a breach and of these 71% say a primary third-party vendor would NOT contact them about a data breach. The cost of a data breach can be crippling to any business continuity plan.
Audited data privacy policies and global industry data security standards are regulated with punitive consequences for non-compliance. The care of duty and the risk rests with the data controller (the originator and caretaker of the data). Well prepared risk programs that include efficient vendor management will mitigate risk when balanced with a responsible cyber and liability insurance investment.

Benefits that iTracker will Deliver

Identify unauthorized access
P3 iTracker identifies transfers of data for registered outsourced processes.

Reduce vendor management cost
All Vendor SLA’s relating to single processes in one place to make contract audits more cost efficient.

Assured Business Continuity
Remove risk and identify vendors who are not delivering business critical service process.

Cyber crime uses assets you trust
Remove channels that offer cyber criminal agents a back door into your mission critical systems

Extend existing data security investments
Our iTracker foundation solution is easily layered into other sophisticated security platform investments

Take charge of your data supply chain
By excluding unqualified vendors your legitimate partners will invest in your business continuity strategy
An introductory guide to inbound marketing
Get to grips with marketing in the digital age
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat.

YOU CAN USE THIS SECTION TO SAY SOMETHING AWESOME
Interesting Title About The Benefits of Your Services
Probes have recorded unusual levels of geological activity in all five planetary systems.
01.
You are in control
Rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere. Lorem ipsum dolor sit amet, consectetur adipiscing elit
02.
You are in control
Rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere. Lorem ipsum dolor sit amet, consectetur adipiscing elit
03.
You are in control
Rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere. Lorem ipsum dolor sit amet, consectetur adipiscing elit
03.
You are in control
Rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere. Lorem ipsum dolor sit amet, consectetur adipiscing elit
.png?width=679&height=250&name=P3%20Audit%20New%20Logo%20(No%20Tag1).png)




-1.png?width=250&height=92&name=P3%20Audit%20New%20Logo%20(No%20Tag1)-1.png)